Generating A Public Key From A Private Key
Generating Keys for Encryption and Decryption.; 3 minutes to read +7; In this article. Creating and managing keys is an important part of the cryptographic process. Symmetric algorithms require the creation of a key and an initialization vector (IV). The key must be kept secret from anyone who should not decrypt your data. Generating the Public Key - Windows 1. At the command prompt, type the following: openssl rsa -in rsa.private -out rsa.public -pubout -outform PEM 2. The public key is saved in a file named rsa.public located in the same folder. Generating the Private Key - Linux 1. Open the Terminal. Navigate to the folder with the. Mar 28, 2018 Generating RSA-SSH Public Key, OpenSSH & PuTTY Compatible Private Keys using PuTTYgen. In a consideration of security, most of the remote SSH connectivity are now transforming to Password-less RSA Authentication. Basically in this method, authentication is being done on the basis of Private / Public key. In which, Server will have a Public Key.
- Generating A Public Key From A Private Keyboard
- Generating A Public Key From A Private Key Club
- Generate A Public Key
- Once the progress bar becomes full, the actual key generation computation takes place. This may take from several seconds to several minutes. When complete, the public key should appear in the Window. You can now specify a passphrase for the key. You should save at.
- How to generate public/private key in C#. Asymmetric cryptography also known as public-key encryption uses a public/private key pair to encrypt and decrypt data. In.NET, the RSACryptoServiceProvider and DSACryptoServiceProvider classes are used for asymmetric encryption.
Creating and managing keys is an important part of the cryptographic process. Symmetric algorithms require the creation of a key and an initialization vector (IV). The key must be kept secret from anyone who should not decrypt your data. The IV does not have to be secret, but should be changed for each session. Asymmetric algorithms require the creation of a public key and a private key. The public key can be made public to anyone, while the private key must known only by the party who will decrypt the data encrypted with the public key. This section describes how to generate and manage keys for both symmetric and asymmetric algorithms.
Symmetric Keys
The symmetric encryption classes supplied by the .NET Framework require a key and a new initialization vector (IV) to encrypt and decrypt data. Whenever you create a new instance of one of the managed symmetric cryptographic classes using the parameterless constructor, a new key and IV are automatically created. Anyone that you allow to decrypt your data must possess the same key and IV and use the same algorithm. Generally, a new key and IV should be created for every session, and neither the key nor IV should be stored for use in a later session.
To communicate a symmetric key and IV to a remote party, you would usually encrypt the symmetric key by using asymmetric encryption. Sending the key across an insecure network without encrypting it is unsafe, because anyone who intercepts the key and IV can then decrypt your data. For more information about exchanging data by using encryption, see Creating a Cryptographic Scheme.
The following example shows the creation of a new instance of the TripleDESCryptoServiceProvider class that implements the TripleDES algorithm.
When the previous code is executed, a new key and IV are generated and placed in the Key and IV properties, respectively.

Sometimes you might need to generate multiple keys. In this situation, you can create a new instance of a class that implements a symmetric algorithm and then create a new key and IV by calling the GenerateKey and GenerateIV methods. The following code example illustrates how to create new keys and IVs after a new instance of the symmetric cryptographic class has been made.
Rsa key generation in javascript. A good passphrase should be at least 10 characters long. You should make sure that the key can only be read by you and not by any other user for security reasons.Next you’ll be prompted to enter a passphrase. Each generated key can be protected by a passphrase. When a key is generated with a passphrase, the key can’t be used without the passphrase, so by using a passphrase one can prevent others from using his private keys without first guessing the passphrase.
When the previous code is executed, a key and IV are generated when the new instance of TripleDESCryptoServiceProvider is made. Another key and IV are created when the GenerateKey and GenerateIV methods are called.
Asymmetric Keys
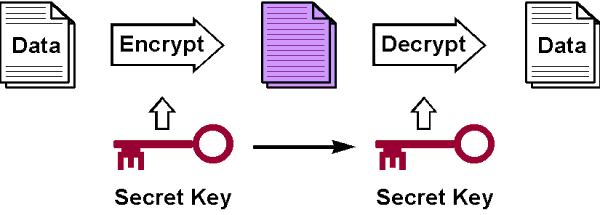
The .NET Framework provides the RSACryptoServiceProvider and DSACryptoServiceProvider classes for asymmetric encryption. These classes create a public/private key pair when you use the parameterless constructor to create a new instance. Asymmetric keys can be either stored for use in multiple sessions or generated for one session only. While the public key can be made generally available, the private key should be closely guarded.
A public/private key pair is generated whenever a new instance of an asymmetric algorithm class is created. After a new instance of the class is created, the key information can be extracted using one of two methods:
The ToXmlString method, which returns an XML representation of the key information.
The ExportParameters method, which returns an RSAParameters structure that holds the key information. Ark survival evolved license key generator.
Both methods accept a Boolean value that indicates whether to return only the public key information or to return both the public-key and the private-key information. An RSACryptoServiceProvider class can be initialized to the value of an RSAParameters structure by using the ImportParameters method.
Asymmetric private keys should never be stored verbatim or in plain text on the local computer. If you need to store a private key, you should use a key container. For more on how to store a private key in a key container, see How to: Store Asymmetric Keys in a Key Container.
The following code example creates a new instance of the RSACryptoServiceProvider class, creating a public/private key pair, and saves the public key information to an RSAParameters structure.
Generating A Public Key From A Private Keyboard
See also
A lost SSH public-key or a web service generates an SSH key but does not provide the public-key part to you. What to do now? There is a solution for this situation.
When you have an SSH key you need the public key to setup SSH passwordless login with SSH-key. But if you have lost the public key part but still have the private key, there is a way to regenerate the key.
With the public key missing, the following command will show you that there is no public key for this SSH key.
The -l option instructs to show the fingerprint in the public key while the -f option specifies the file of the key to list the fingerprint for.
To generate the missing public key again from the private key, the following command will generate the public key of the private key provided with the -f option.
The -y option will read a private SSH key file and prints an SSH public key to stdout. The public key part is redirected to the file with the same name as the private key but with the .pub file extension. If the key has a password set, the password will be required to generate the public key.
To check the details of the generated public key execute the following command as shown above.
Generating A Public Key From A Private Key Club
The output of this command shows the key size as the first column, the fingerprint as the second column and after the file name, the type is shown in brackets. In the example above, a 4096 bit RSA key.
Read more of my posts on my blog at http://blog.tinned-software.net/.